Operation Security Is Used to Identify Which of the Following

Security For The Mobile First Era Mobile Threats And Countermeasures Using A Layered Security Approach Data Loss Prevention Mobile Device Management Byod


Nist Revises Guide On Security Controls Security Assessment Business Process System Architecture

Steps To Prepare Data Breach Data Breach Cyber Security Data

Do You Know What Is A Honeypot Infographic Social Media Infographic Computer Technology

Nist Cyber Security Framework Cyber Security Cyber Security Technology Cyber Security Program
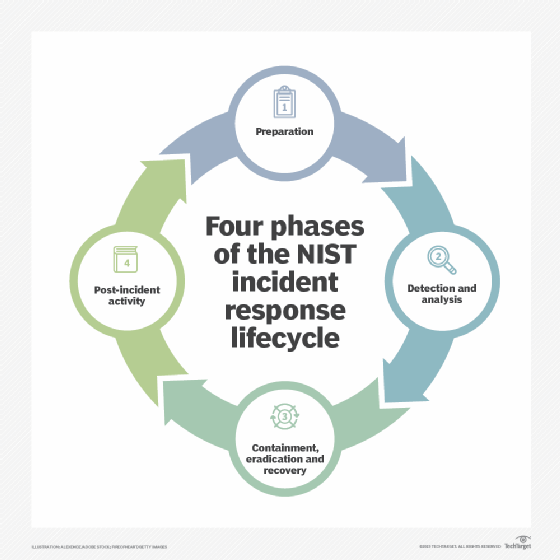
What Is Opsec Operations Security

Software Tools And Services Used To Achieve Iso 27001 Help Net Security Computer Security Cyber Security Awareness Cyber Safety

8 Step Network Vulnerability Assessment Process Vulnerability Cyber Security Program Cyber Security Awareness

Cyber Security Services Suma Soft Cyber Security Security Service Cyber

Hassh A Network Fingerprinting Standard Which Can Be Used To Identify Specific Client And Server Ssh Implementations Networking Server Cyber Security

We Used Cb Insights To Identify Over 80 Private Companies In Cybersecurity That Are Using Ai And Categorized Cyber Security Startup Marketing Mobile Security

Door Access Control Gsm Mobile Phone Remote Control Door Opener Sms Door Control In 2022 Caller Id Access Control Remote Controls

Infographic 8 Cybersecurity Commandments Workers Should Follow Cyber Security Awareness Cyber Security Cyber Security Education

Security Analytics User And Entity Behavior Analytics Ueba Which Identifies Threats Amp Anomalies Cyber Security Digital Advertising Agency Business Data

Vulnerability Management Services Vulnerability Management Is A Drain On Your Security Team Scans Take Too Long Vulne Vulnerability Management Cyber Security

The Business Case For Operational Technology Cybersecurity Cyber Security Business Continuity Planning Business Case
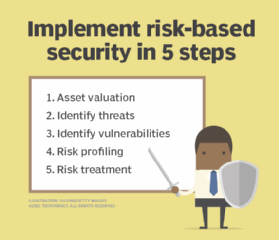
What Is Opsec Operations Security

Cyber Advisor Cycle Graphic 600x600 Cyber Threat Intelligence Threat Cyber

Nist Cybersecurity Framework Cybersecurity Framework Cyber Security Security Consultant

Comments
Post a Comment